Qualiphy (Healthcare – Amazon EKS + RDS + Compliance)
Standardizing Secure CI/CD and Infrastructure Automation for a Telehealth Platform on AWS
Executive Summary
Qualiphy is a leading telehealth solutions provider, empowering medspas and clinics with compliant, secure, and seamless virtual care. To support their rapid growth and ensure a scalable, compliant infrastructure, Qualiphy needed to modernize its AWS environment and implement best practices for governance, security, and automation. They required a well-architected multi-account setup to isolate production and non-production workloads, streamline deployments, and meet strict healthcare compliance standards.
GoCloud partnered with Qualiphy to implement account provisioning, and security guardrails. In addition, GoCloud modernized Qualiphy’s containerized workloads on Amazon EKS with a fully integrated CI/CD pipeline, ensuring consistent, secure deployments across environments. This foundation now enables Qualiphy to deliver telehealth services at scale, maintain regulatory compliance, and provide a reliable, high-quality experience for clinics and their patients worldwide.
About the Customer
About Qualiphy
Qualiphy is a leading telehealth solutions provider, empowering medspas and clinics with compliant, secure, and seamless virtual care. To support their rapid growth and ensure a scalable, compliant infrastructure, Qualiphy needed to modernize its AWS environment and implement best practices for governance, security, and automation. They required a well-architected multi-account setup to isolate production and non-production workloads, streamline deployments, and meet strict healthcare compliance standards.
Customer Challenge
Infrastructure provisioning
Infrastructure provisioning was largely manual, leading to inconsistent deployments, increased operational overhead, and higher risk of misconfiguration
Multi-account governance
Multi-account governance and environment isolation were limited, making it difficult to enforce security, compliance, and access controls.
Containerized workloads
Containerized workloads and orchestration were not standardized, resulting in inefficient application scaling and resource utilization
Backup
Backup, recovery, and monitoring processes were inconsistent, increasing the risk of downtime and data loss.
Security
Security and compliance controls, including credential management, encryption, and policy enforcement, were handled manually, raising the potential for errors and unauthorized access.
Why Amazon
Web Services
AWS provides a depth and breadth of infrastructure capabilities and tech technological offerings that are unparalleled. GoCloud chose AWS as their cloud provider because of high-performance, resiliency, scalability, and agility benefits the platform has to offer. Moreover, leveraging the latest AWS tools and technologies would streamline their workflows and result in a decreased time to market for their software products.
Why Qualiphy
Chose GoCloud
GoCloud’s Solution
Services Used
Amazon EKS →
Managed Kubernetes clusters for Dev, Stage, Release and Prod with high availability and auto-scaling.
AWS CodePipeline →
Automated CI/CD pipelines integrated with Bitbucket for continuous delivery.
AWS CodeBuild →
Builds and tests application code as part of the CI/CD workflow.
Stores and manages Docker
Amazon ECR → container images for deployment into EKS.
Amazon RDS MySQL (Multi-AZ) →
Highly available relational database with daily backups, storage auto-scaling, and point-in-time recovery.
AWS Secrets Manager →
Secure storage, rotation, and encryption of database and application credentials.
Elastic Load Balancer (ELB/ALB) →
Distributes traffic across EKS worker nodes and ensures resilience
Amazon VPC (private subnets) →
Isolated network architecture for worker nodes, databases, and sensitive workloads.
AWS NAT Gateway →
Provides redundant outbound internet access for resources in private subnets.
AWS Backup →
Centralized backup for RDS MySQL with daily snapshots and 7-day retention.
AWS Systems Manager →
Centralized operations management, automation, and patching for workloads.
Amazon S3 →
Scalable storage for CI/CD artifacts, logs, and state filesacross environments.
AWS CloudFormation →
Infrastructure as Code (IaC) for consistent, repeatable provisioning of all environments
Amazon CloudWatch →
Monitoring, logging, and performance metrics for EKS, RDS, and application workloads.
Architecture Diagram
Workflow
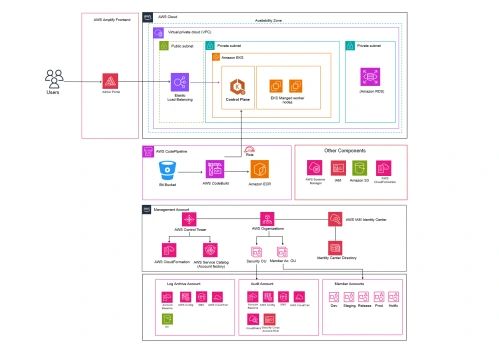
For this environment, a structured multi-account setup was provisioned to support Dev, Stage, Release and Prod environments, each running in a dedicated Amazon VPC spanning multiple Availability Zones (AZs) to ensure resilience, security, and high availability. All resources are provisioned and maintained through AWS CloudFormation, ensuring Infrastructure as Code consistency across environments.
In the development environment, applications run in Amazon EKS clusters with CI/CD fully automated through AWS Code Pipeline, which integrates with Bitbucket and AWS Code Build. Docker images are stored in Amazon ECR, and new builds are automatically deployed into the cluster. The staging environment mirrors production closely, with EKS worker nodes deployed in private subnets behind an Elastic Load Balancer and integrated with an Amazon RDS MySQL database running in a private subnet with daily backups and 7-day retention. The CI/CD pipeline follows the same flow, ensuring every deployment tested in staging reflects production behavior. In production, highly available EKS clusters run across multiple AZs and serve traffic through an Elastic Load Balancer, while RDS MySQL operates in Multi-AZ mode with automated failover, daily backups, and secure credential management through AWS Secrets Manager.
The network architecture enforces private subnet isolation for all worker nodes, databases, and sensitive workloads. Access is tightly controlled through IAM roles, NAT gateways, and security groups, with AWS Secrets Manager ensuring that credentials remain encrypted, rotated, and centrally managed. Supporting services such as AWS Systems Manager, IAM, S3, and CloudFormation provide centralized management, secure storage, and governance.
The environment is designed with high availability and failure resilience in mind. EKS worker nodes and RDS MySQL are deployed across multiple AZs, with Elastic Load Balancing distributing traffic only to healthy nodes. Amazon EKS leverages AWS’s managed control plane for fault tolerance, while NAT gateways ensure resilient outbound connectivity. At the database layer, MultiAZ RDS MySQL ensures automatic failover, with AWS Backup providing daily snapshots and 7-day retention for point-in-time recovery. During failover or node replacement, Secrets Manager ensures uninterrupted reconnections between applications and services.
Scalability is achieved at every layer. Amazon EKS worker nodes auto scale based on CPU, memory, and custom application metrics in both Stage and Prod. Elastic Load Balancers automatically adapt to traffic spikes, and RDS MySQL supports both storages auto-scaling and read replicas to handle growing workloads. Code Pipeline manages deployments seamlessly, while Amazon S3 provides near-infinite scalability for artifacts, logs, and state files. Secrets Manager scales transparently to manage growing application secrets.
The design balances tradeoffs between Multi-AZ and Multi-Region. The current strategy favors Multi-AZ for cost-efficiency, with AWS Backup configured for cross-region recovery if needed. Similarly, managed services like Amazon EKS, RDS MySQL, and Secrets Manager are leveraged to reduce operational overhead while ensuring reliability and security. Private subnet architecture strengthens data protection but requires precise NAT Gateway and Secrets Manager integration for outbound access and connectivity.
The overall architecture is validated with evidence artifacts, including a multiaccount architecture diagram showing Dev, Stage, Release and Prod environments with EKS, RDS MySQL, Elastic Load Balancers, Code Pipeline, Code Build, and Amazon ECR. Documentation highlights HA and scalability features such as Multi-AZ deployments, RDS MySQL daily backups, EKS auto scaling, and Secrets Manager integrations. Failure handling is addressed comprehensively across the application, database, networking, and credential layers. With AWS Backup, CloudFormation, and Secrets Manager forming the backbone of resilience and automation, this environment ensures that applications remain highly available, secure, and easily recoverable.
Results & Benefits
• Automated Infrastructure Provisioning
Infrastructure is now provisioned through CloudFormation, ensuring repeatable, consistent deployments, reducing operational overhead, and minimizing misconfiguration risks.
• Centralized Multi-Account Governance
AWS Control Tower provides multi-account governance, enforcing security guardrails, environment isolation, and compliance across Dev, Staging, and Production accounts.
• Standardized Container Orchestration
Amazon EKS standardizes container orchestration, enabling efficient scaling, resource utilization, and reliable deployment of applications across environments.
• Reliable Backup and Recovery
RDS and CloudFormation-managed resources leverage automated backup, recovery, and monitoring processes, reducing downtime risk and ensuring data protection.
• Enhanced Security and Compliance
AWS Secrets Manager centralizes credential management with automated rotation, while encryption at rest (KMS) and in transit (SSL/TLS), combined with Control Tower governance, ensures consistent security and compliance enforcement.